Digital Forensics
Chain of custody
Why use chain of custody?
A chain of custody is meant to secure the integrity of the electronic evidence related to a digital forensic case. Securing the chain from first contact to storage and returning evidence means lowering the potential risk of other people and professionals doubting your work methods. Another benefit of using a chain of custody is to note down and keep track of people and organizations involved in the ongoing case. Adding time, date and location also allows for different parties to follow when and where the evidence was handled.
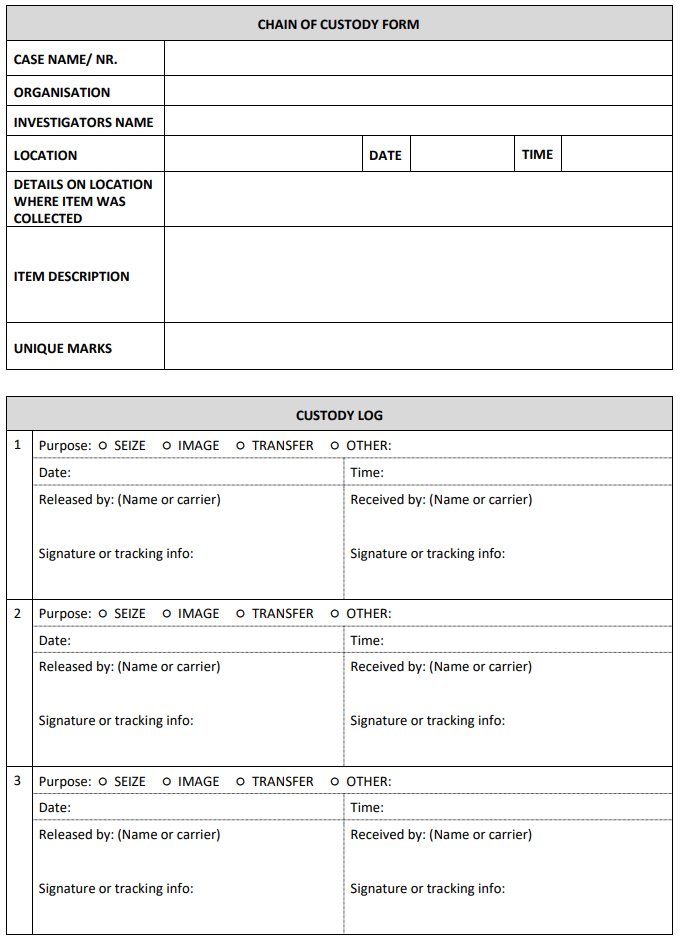
Another point that should be included in the chain of custody is to add the case number related to the evidence as well as a description of the physical evidence media. Include any unique marks, traits, colors, text or attached objects that can be used to describe the physical evidence media. The last item to add is the custody log. This log is the list that tracks all the people, times and locations that has been involved in the evidence handling. This list should show who gave away the evidence and who received the evidence by adding a signature from both parties. The log should also note the action taken eg. imaged, seized or another action at the time.
Each time the custody log is appended, the chain of custody should be handed over along with the evidence item. The person handing over the evidence may keep a copy of the chain of custody as a reference or receipt of the previous actions. This is also to ensure other people and parties (that were not present) that the person did in fact, hand the evidence over to the next custodian. This way, the person previously responsible for the evidence is not to blame if wrongful action were taken towards the evidence after the transfer.
Example of a generic chain of custody
This sample form of a chain of custody covers the essential parts that should be included.
Download document: PDF file